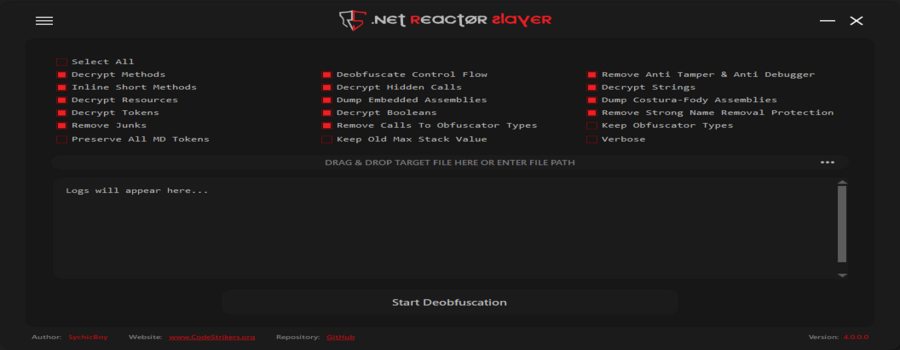
.NETReactorSlayer is an open source (GPLv3) deobfuscator for Eziriz .NET Reactor.
Features & Commands:
| Command | Description | Default Value |
|---|---|---|
| Unpack native stub | ||
--dec-methods | Decrypt methods that encrypted by Necrobit | True |
--dec-calls | Decrypt hidden calls | True |
--dec-strings | Decrypt strings | True |
--dec-rsrc | Decrypt assembly resources | True |
--dec-tokens | Decrypt tokens | True |
--dec-bools | Decrypt booleans | True |
--deob-cflow | Deobfuscate control flow | True |
--dump-asm | Dump embedded assemblies | True |
--dump-costura | Dump assemblies that embedded by Costura.Fody | True |
--inline-methods | Inline short methods | True |
--rem-antis | Remove anti tamper & anti debugger | True |
--rem-sn | Remove strong name removal protection | True |
--rem-calls | Remove calls to obfuscator methods | True |
--rem-junks | Remove junk types, methods, fields, etc… | True |
--keep-types | Keep obfuscator types, methods, fields, etc… | False |
--preserve-all | Preserve all metadata tokens | False |
--keep-max-stack | Keep old max stack value | False |
--no-pause | Close CLI immediately after deobfuscation | False |
--verbose | Verbose mode | False |
Usage:
Just drag and drop target obfuscated assembly on it.
Known Issues:
If target assembly not working after deobfuscation try using
--preserve-alland/or--keep-max-stackcommand(s).Since .NETReactorSlayer does not yet have the ability to de-virtualize virtualized functions, if the target protected assembly contains virtualized functions, .NETReactorSlayer may fail to de-obfuscate some protections such as string encryption and control flow.
➡️Click to see few example of comparing virtualized functions with normal functions
 |
| 
 |
| 
Contribution:
Want to contribute to this project? Feel free to open a pull request.
License:
.NETReactorSlayer is licensed under GPLv3.